Firewall Scanning
Know what’s available on your firewalls.
Get a complete picture of the ports and services accessible from the internet, so you can reduce the unnecessary exposures that attacker’s target.
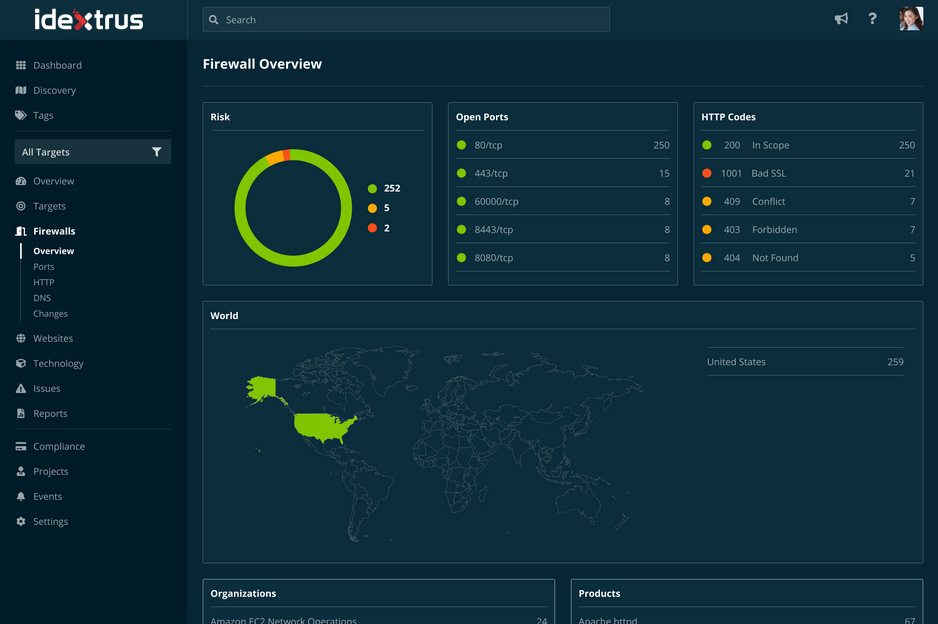
Every service available on your firewall is another doorway to a potential breach. Monitoring and closing unnecessary ports can help reduce your attack surface, as well as the workload associated with cleaning up vulnerabilities that might exist on the services.
With Firewall Scanning, we highlight each type of service using risk indicators to help you prioritize which ones are exposing you to the greatest risk. And by consistently monitoring for new services coming online, you can make sure to put in the appropriate controls and scan them as necessary.
Detect, catalog and monitor
Website Scanning
Monitor the security posture of your websites.
Continuously track your certificates, HTTP headers, third-party scripts, and more with up-to-date data across all your websites.
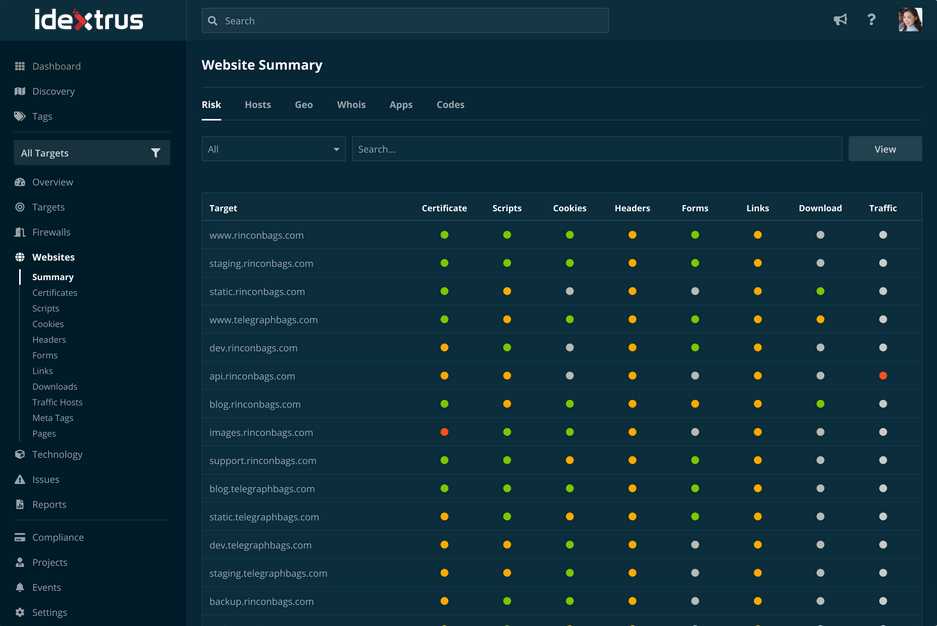
While websites are essential to most businesses, they create security risks that attackers target. Strong security practices across your websites can help mitigate the effects of many types of attack. Website Scanning lets you easily look across your websites to assess the strength of security controls in place and ensure that your sites and users are protected.
Detect, catalog and monitor
Technology Scanning
Monitor the technologies you rely on.
Identify the third-party software, platforms, and infrastructure your external assets rely on.
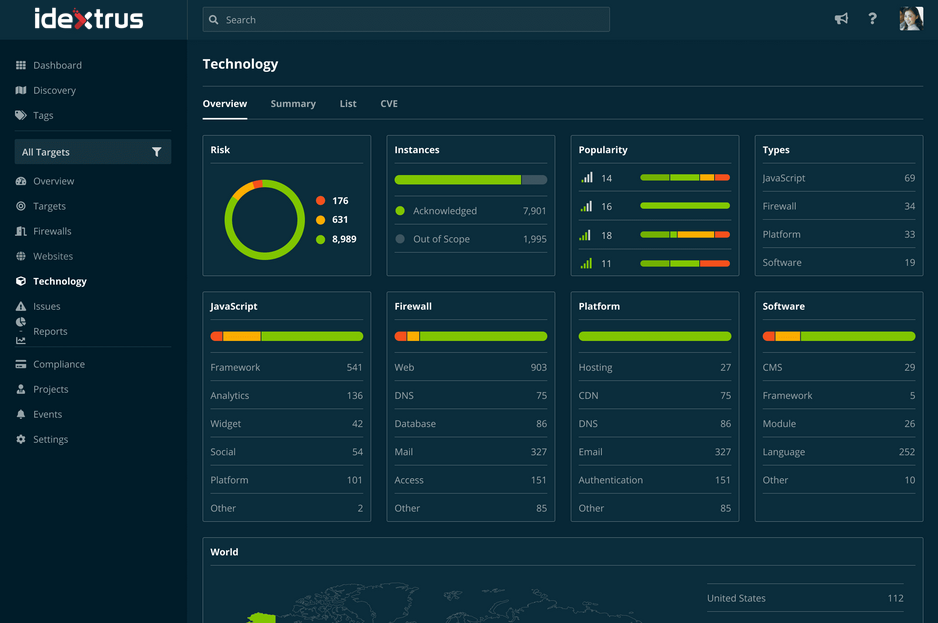
Businesses increasingly look to third-party vendors and solutions to build better software and services. But keeping track of what you're running can be a challenge. Technology Scanning detects and catalogs the various platforms, libraries, software, and systems your external assets are running. Advanced fingerprinting allows better classification and version detection, helping you monitor what technologies you have in place.
Use Cases
Server Scanning
Find your server vulnerabilities.
Detect vulnerabilities, missing security patches, and out-of-date software across all your external servers.
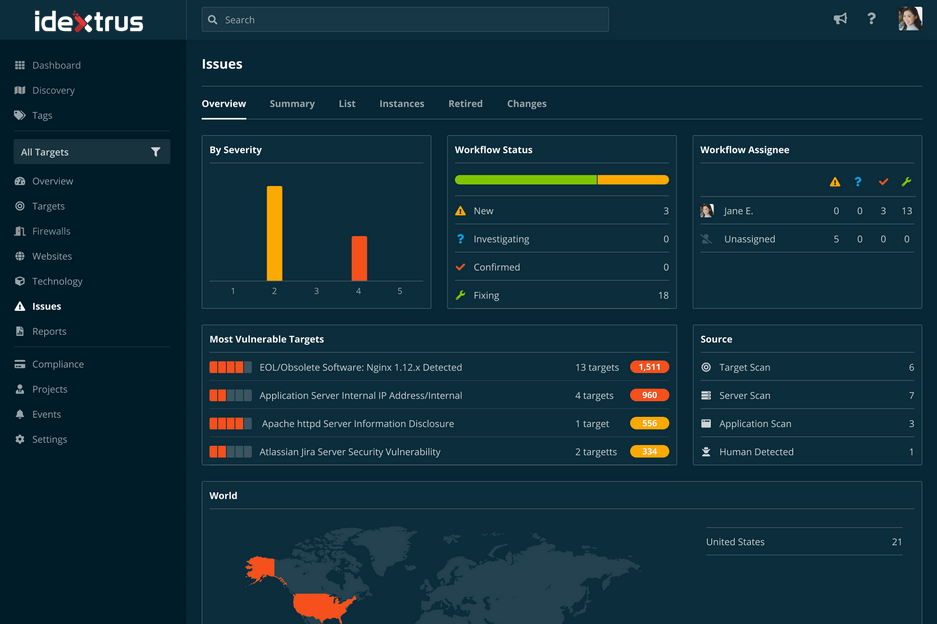
Server security issues and misconfigurations make your business susceptible to costly breaches. That's why our Server Scanning helps you identify known security issues on your perimeter before the attackers do.
Our vulnerability database is constantly updated, helping you detect the latest vulnerabilities. In just minutes we’ll help you discover open ports, exposed services, missing security patches, and configuration weaknesses that put you at risk. Once we discover your vulnerabilities, we'll let you know which are most critical to resolve, and help you remediate them quickly.
Automatically Detect
Application Scanning
Secure your web applications.
Identify coding flaws and security weaknesses on your websites and applications that could be used to exploit your business.
Detecting vulnerabilities in your custom web applications is critical as they can pose a significant risk to your business. By proactively testing the security of your web applications, you can stay ahead of attackers and protect your valuable assets.
Application Scanning uses the Dynamic Application Security Testing (DAST) approach to help you discover custom web application vulnerabilities such as SQL Injection, Cross-Site Scripting, Cross-Site Request Forgery, and OWASP Top 10 Security Risks, and SANS CWE TOP 25 Most Dangerous Software Errors.

